LoRaWAN® Is Secure (but Implementation Matters)
By LoRa Alliance® Technical Committee
Securing an Internet of Things (IoT) deployment and keeping it safe and secure is not only a matter of choosing the right protocol, it relies on the implementation process as well as embracing best practices and industry standards.
LoRaWAN is by design very secure—authentication and encryption are, in fact, mandatory—but networks and devices can be compromised if security keys are not kept safe, not randomized across devices or if cryptographic numbers used once (nonces) are reused, as is shown by numerous blog posts. That’s why it is critical to look for LoRaWAN CertifiedCM devices to ensure the device has been tested against the standard and works as expected.
The LoRa Alliance has always kept security front and center in its development of the LoRaWAN specification and has been highly transparent about the protocol’s security features (see Figure 1). The LoRaWAN specification has been designed from the outset with security as an essential aspect, providing state-of-the-art security properties that meet the needs of highly scalable low-power IoT networks. Unlike many other IoT technologies, the LoRaWAN specification already offers dedicated end-to-end encryption to application providers.
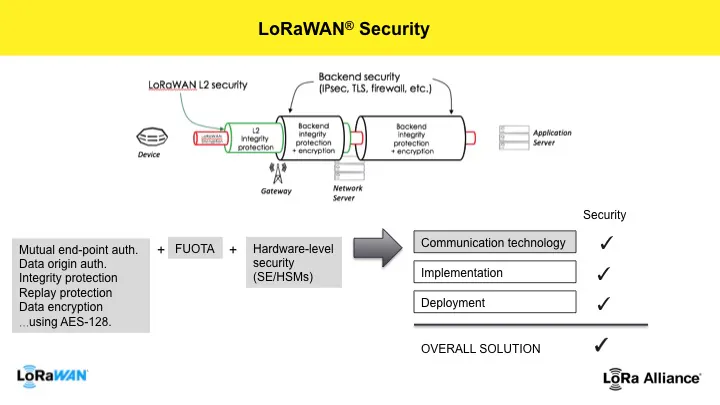
Figure 1: LoRaWAN security overview
The specification defines two layers of cryptography:
Using a unique 128-bit network session key shared between the end-device and network server
Using a unique 128-bit application session key (AppSKey) shared end-to-end at the application level
AES algorithms are used to provide authentication and integrity of packets to the network server and end-to-end encryption to the application server. By providing these two levels, it becomes possible to implement “multitenant” shared networks without the network operator having visibility of the users’ payload data. The devices can be activated by Personalization on the production line or during commissioning, or can be over the air activated (OTAA) in the field. OTAA allows device sessions to be rekeyed if necessary.
LoRaWAN has all the fundamental building blocks required and used by any modern wireless communications technology, and does so at AES-128 strength. LoRaWAN’s inherent security, as provided in the specification, needs to be accompanied by secure implementation and secure deployment of these devices and/or networks to maintain the protocol’s built-in security mechanisms. It should be pointed out that this is true of all secure device implementations using any communication technology.
As stated above, LoRaWAN relies on symmetric cryptography, which requires sharing keys in a safe and secure way. To further aid with this process, LoRa Alliance members have developed:
LoRaWAN backend interfaces that isolate the storage of root keys in the join server, so that becomes a trusted player, regardless of network
Secure element solutions that provide additional hardware physical protection against tampering
To ensure device and network security, as with any technology, the best practice is always to use certified devices and work with proven and trusted service providers. LoRaWAN is no different, and end users can be confident in their deployment if they leverage resources that know how to correctly implement LoRaWAN solutions.
Security is a constantly moving target, with malicious actors continuously appearing, and LoRaWAN is always evolving to meet any new threats as well. Though LoRaWAN is inherently secure, the LoRa Alliance is constantly reviewing, designing and implementing security enhancements and best practices to ensure LoRaWAN stays ahead of the changing security landscape.
As such, and to assist the market in choosing the right implementation, the LoRa Alliance will publish a Recommended Practices document in the next month that will provide best practices for device makers to keep their devices secure. In addition, the Security Working Group, reporting to the LoRa Alliance Technical Committee responsible for the LoRaWAN specification, continuously reviews security aspects of technical specifications and documents. The Security Working Group consists of security experts from the LoRa Alliance membership and works with academia to review papers and discuss security challenges.
For more information about LoRaWAN security, please check out our updated Security FAQs, which address the common questions about how the specification has implemented security features.
LoRa Alliance®, LoRaWAN® and LoRaWAN CertifiedCM are registered trademarks.